[ELTEX] - Devices NTP-RG-1402G & NTP-2 - OS command Injection - (CVE-2020-9026/CVE-2020-9027)
Devices NTP-RG-1402G & NTP-2 presents a vulnerability of injecting OS commands into the input PING and TRACE of the resource "ping.cmd", which allows an attacker to execute commands in the operating system and gain access to the server via remote shell.
NTP-RG-1402G
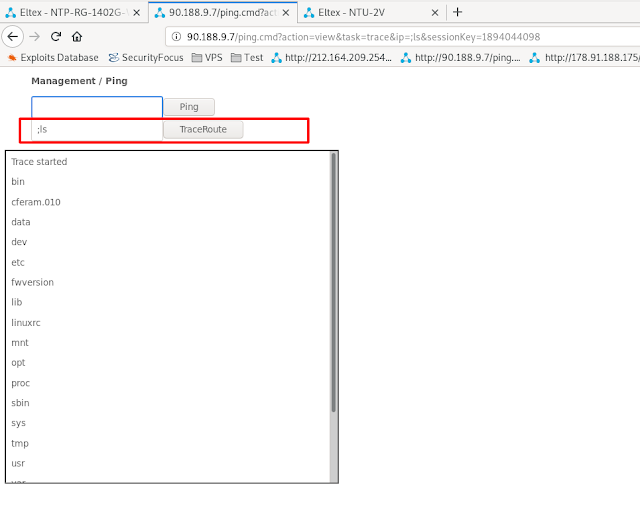
Well, reviewing the application, I found an interesting function called "Ping", once we click on it, we have two options or commands, PING and TRACE. So I try the old reliable by injecting ";" and "|" followed by an operating system command, in this case "; ls" in both the PING command and the TRACE command, and it turns out that it shows me the list of files in both cases.
Once the command injection has been confirmed I try to read the /etc/passwd
Perfect, now how about loading a shell? .. well, for this I use wget, I assign permissions to the binary and run
NTP-2
With the NTP-2 device, coincidentally these "PING and TRACE" functions, so I repeat procedure and inject a "ls" to test and both functions are vulnerable, so I repeat the procedure to obtain reverse shell.
Downloading, executing and obtaining the reverse shell
Affected Devices:
- NTP-RG-1402G - Hardware Version 1v10 - Software Version - 3.25.3.32
- NTP-2 - Hardware Version 1v5:B+10 - Software Version - 3.25.1.1226
CVE-2020-9026
CVE-2020-9027
By: @Linuxmonr4












Comentarios
Publicar un comentario